Xmaze Pen-Testing
Xmaze AI Pen-Testing Extension
Next-Gen Automated Penetration Testing Platform Driven by AI multi-engine

Add a small xmirror
Answer your questions
White Hat's Sharp Blade
Persistent Threat Simulation and Security Measurement Platform (Xmaze PTE) closely combines AI technology with hacker attack technology, and uses RNN deep learning algorithms to simulate hacker intrusions. It can provide users with continuous network security verification and vulnerability mining capabilities, helping users verify the effectiveness of security controls.
The Evolution of Vul-Detection
Traditional vulnerability detection methods mainly include vulnerability scanning products and expert penetration testing. The detection capabilities of vulnerability scanning products are based on rules, so they can only detect conventional component vulnerabilities and injection vulnerabilities, and are powerless against business logic vulnerabilities that cannot extract features.In the field of expert penetration testing, it mainly relies on the expert experience of white hat hackers to identify and verify business logic vulnerabilities through manual analysis. However, the cost of labor is high, the level is uneven, and the detection rate and vulnerability coverage are difficult to be effectively guaranteed. Therefore, the next generation of vulnerability detection technology needs to be based on AI technology, combining the advantages of vulnerability scanning products and expert penetration testing, using expert capabilities for AI training, and realizing accurate detection of business logic vulnerabilities in an automated or semi-automated manner. Artificial intelligence is no longer a fantasy, but an indispensable basic capability in the next generation of vulnerability detection products. The future is here.

Professional
Pen-Testing Bot
Xmaze PTE is designed for government and enterprise security departments, operation and maintenance management departments, network red teams, white hat hackers and other professionals. It creatively transforms the practical experience accumulated by white hats in a large number of penetration processes into structured experience that can be stored, identified and processed by machines. In the process of automated penetration testing, it uses artificial intelligence algorithms to continuously grow "intelligence" and make logical reasoning decisions, and conducts a complete penetration process from information collection to vulnerability exploitation on the target in a way close to actual manual penetration.
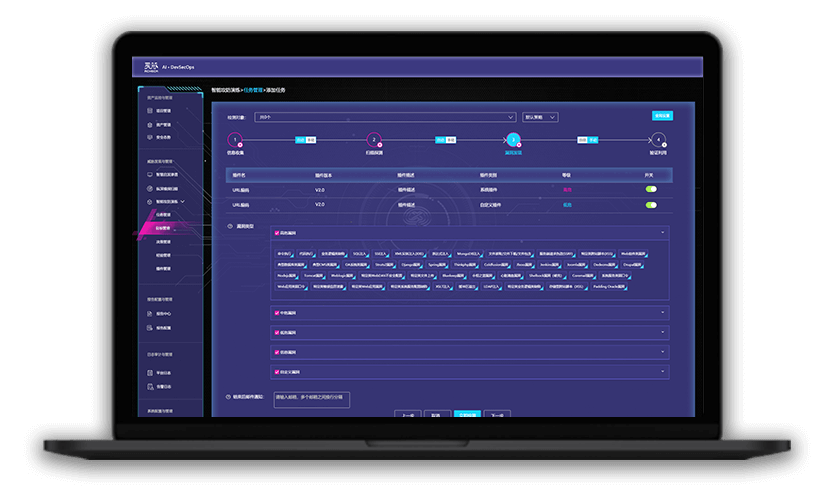
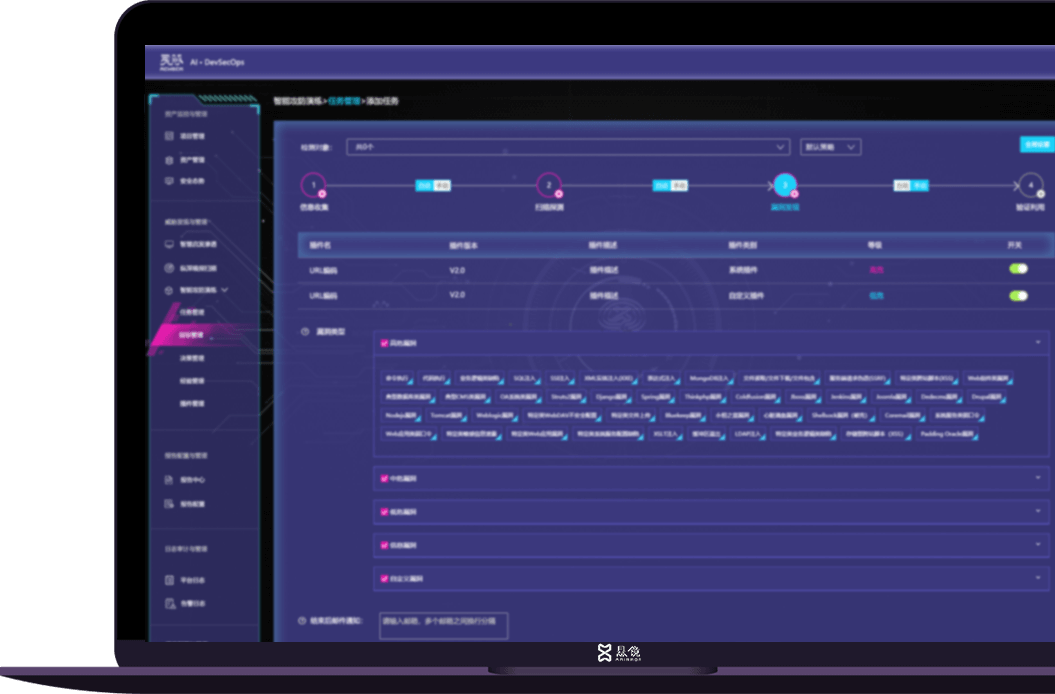
Intelligent Attack & Defense Drill
Use hacker language to input penetration experience, and conduct intelligent attack and defense drills based on decision linkage. Create a unique "hacker language" to digitally store massive penetration logic. Penetrators can use the syntax of "hacker language" to write experience, structure abstract penetration test experience, and make Xmaze PTE a powerful extension of penetration testers' combat power.

Refined Task Management
Through the task panorama, the penetration process of the target is displayed in real time and graphically, helping penetration testers to grasp the penetration progress in real time. During the penetration process, penetration testers can adjust task parameters according to the progress of the test, so that automation and personalization are fully integrated and unified.

Intelligent Closed-loop Penetration Management

Reject High Cost and Inefficiency
According to reports from authoritative organizations, the TSI (Talent Scarcity Index) of security experts is as high as 3.1, which means that nearly 70% of job vacancies cannot be filled, which directly leads to high salaries for security experts, further pushing up the cost of expert penetration testing. In addition, the purely manual implementation method makes it difficult for traditional expert penetration testing services to meet the actual needs of DevOps agile development. Xmaze PTE replaces security experts with AI expert systems and replaces manual experience reserves with deep learning capabilities, making low-cost and high-efficiency penetration testing a reality.

*The above legend is based on a five-year service period estimation of a medium-sized website using Xmaze's standard products.
Clients
The original, patented Fourth-generation DevSecOps digital supply chain security management system, incorporating an "Multimodal SCA+DevSecOps+SBOM risk intelligence early warning ",Innovatively empowers users across various industries such as finance, connected vehicles, telecommunications, energy, government, smart manufacturing, and the broader Internet sector. This system builds a symbiotic and proactive defense framework that adapts to business elasticity, supports agile business delivery, and guides future architectural evolution, continuously safeguarding the security of china's digital supply chain.
Partners
Together with our partners, we are exploring a billion-dollar blue ocean market, jointly driving the implementation of DevSecOps digital supply chain security practices for enterprises, and fostering a symbiotic relationship between business growth and security.
Comments
Awards
-

China Top 50 Technology Companies
-

Forrester
SCA、SAST Evaluated Vendors
-

International Data Corporation
China DevSecOps Innovators
-
Gartner
SCA Evaluated Vendors
-

CDM Group
Next-Gen in Open-Source Security
-

Business Intelligence Group
BIG Innovation Award
-

Internet Security Conference
The Top 10 Innovators of the Year
-

China Academy of Information and Communications Technology
Software Supply Chain Famous Achievement Cases
Certifications
-

National high-tech enterprise
-

CNNVD compatibility certification
-

CAPPVD vulnerability library support unit
-

Intellectual Property Management System Certification
ddd
-

Beijing Intellectual Property Pilot Unit
-

International Quality Management System Certification
ISO9001
-

International Information Technology Service Management System
ISO20000
-

International Information Security Management System
ISO27001
Threat governance from the application source, building a new generation of Digital Supply Chain Security system












 在线咨询
在线咨询
